If you do not already have a password manager and 2FA authenticator app setup in place, then this guide is for you. We highly recommend you follow all 5 steps carefully to prevent getting hacked – risking to lose your money and identity!
No matter if you are reading this to protect your private life or if you’re a business owner. This guide covers the most important steps that you should do right now. We all want to be safe. To protect ourselves, we take out countless insurance policies. Because it’s better to be safe than sorry, right?
But have you ever thought about threats that can destroy your professional and private life from one day to the other – like hacker attacks and identity theft? Probably not. Precaution is important – and necessary! Because once it happens, it’s already too late.
In this article, we will give you a step-by-step guide to protect yourself from hacker attacks easily and without any costs. Our focus is on simplicity – so that you can actually take action right away.
Our tips will also save you a lot of time in the daily handling of your accounts. You will never forget important passwords ever again and can finally sleep peacefully.
So, let’s get started!
- You Are at Risk of Getting Hacked! - Alarming Stats, Facts And Figures
- What Is Cybercrime? These Are The Top 3 Cyber Security Threats
- The 5 Simple Steps to Secure Your Accounts - Free and Fast
- How to Generate And Save Strong Passwords With "LastPass"
- How to Enable 2FA For Your Logins - Setup & Configure the "Authy" App
- Bonus: 7 Cyber Security Tips for your Business or Private Life
- Conclusion - Stay Safe and Protect Your Data & Accounts
Why Cyber Security Is Important - Alarming Stats, Facts And Figures
It can hit anyone – and you are at risk, too. Hacker attacks on the Internet are increasing rapidly and are the new type of mass crime. On average, every 39 seconds there is a hacker attack of a computer with Internet access, affecting one in three Americans every year – and the number of data breaches is still growing.
Since COVID-19, the US FBI reported a 300% increase in reported cybercrimes.
And the consequences are devastating – because data theft can, in the worst case, ruin you, both in your private life and business life. At stake are for example financial losses of incalculable proportions and lasting damage to your image.
The good news is: You can easily minimize the risk of becoming a victim of a cyber attack – without putting in a lot of effort and completely for free. 95% of cyber security breaches are due to human error. So it’s time to implement appropriate security measures such as two-factor authentication via an Authenticator app, strong and unique passwords as well as a good backup strategy.
What Is Cybercrime? The Top 3 Cyber Security Threats And What They Are About
Wherever devices like computers and smartphones are used, you will find this threat: Cybercrime. Cybercrime means any criminal activity that either targets or uses a computer, a computer network or a networked device. The goal is almost always the criminals’ own (financial) enrichment.
Most cyber attacks are run automatically, meaning that nobody is aiming it specifically towards you. What makes cybercrime so dangerous is that it can be committed from almost anywhere in the world. As a result, it is difficult for authorities to prosecute. So the fact that you live in a generally safe country like the United States, Australia or the UK does not mean your online activities are safe.
Common Types of Hacker Attacks That You And Your Business Are at Risk of Include the Following:
- Email phishing attacks – Phishing is a form of cybercrime in which targets are contacted via e-mail to lure individuals into providing sensitive data. Targets click on a manipulated link and enter their data in a fake website mask, for example a form that looks like Amazon’s login form. The criminals then use the data to gain access to accounts. Your mail account can also be hacked and used to send phishing emails. This may not only have financial consequences for you but also cause lasting damage to your image.
- Online identity theft – Hackers use your data to complete purchases in your name or make money withdrawals e.g. via Ebay, Amazon, PayPal or other accounts. In the worst case, your data may even be sold in the Darknet. You can try to find out whether your email address has ever appeared in one of these lists by using the free service of haveibeenpwned.com. Hackers sometimes get data via mass attacks on free mail services such as Yahoo or AOL for example. So be careful with those accounts! Most security experts recommend to completely delete your old Yahoo account due to the lack of security.
- Hacker attacks on websites – In addition, hacker attacks such as brute force or DDoS attacks are a serious threat to websites. In brute force attacks, random character and letter combinations are entered en masse and at lightning speed until access is ultimately cracked – for example, to inject malware, tap credit card data and serve advertising. A DDoS attack aims to disrupt the server and penetrate your database through it.
Your Digital B2B Marketing Agency
Minimize Your Risk With These Free Cyber Security Tools - In 5 Easy Steps
There are endless possibilities of how hackers can harm you – and as the number of hacker attacks increases, so does their professionalism. However, this does not mean that you are powerless against it. Quite the contrary!
You can protect yourself very well against most cyber attacks – with little effort, and often times even free of charge. Our guide will provide you with a simple step-by-step instruction how to protect your business from the most common hacker attacks.
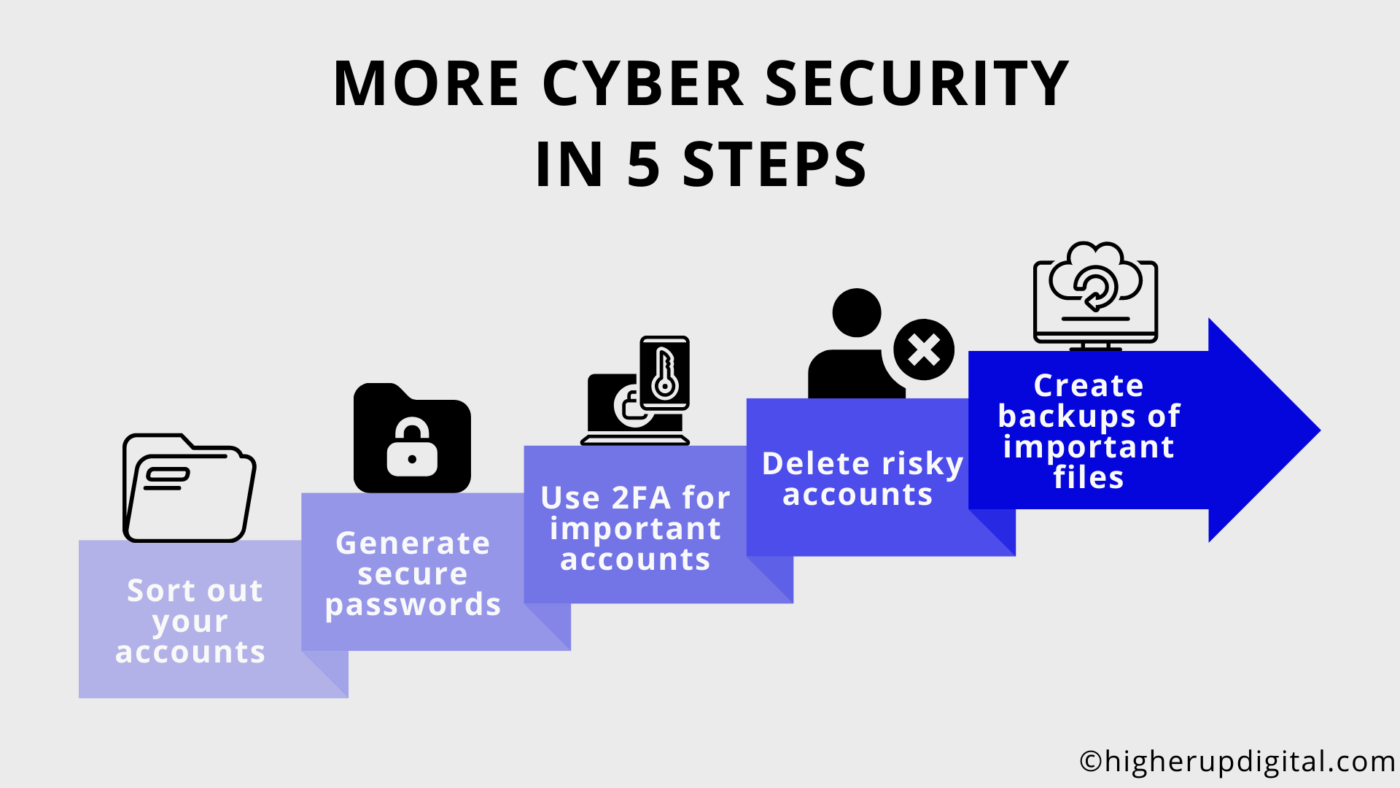
1. Get an Overview of Your Accounts
The first step is to get an overview of your accounts – both business-related and private ones. Write down your answers to the following questions (we recommend to actually use a pen and a piece of paper to pre-sort it): Which email addresses do you use for which accounts and websites? Make a list of all the accounts you are currently using.
Then mark the accounts that are particularly important to you. For example, your Amazon account, your Google account and your email program are probably particularly important to you and threats to those accounts can cause a lot of damage. Accounts for normal online stores on the other hand probably have rather secondary priority.
Your administration accounts, such as your email account, are important as they can be used to recover passwords. So they need to be well secured.
2. Generate a Secure Password for Each Account
Next, each account needs an individual, secure password.
Set a different password for each account, consisting of several characters (letters and numbers). The accounts that you marked as “important” in the previous step should also be secured with two-factor authentication (2FA) via app. Later on in this guide we’ll show you how to create passwords, how to store them and also how to setup your 2FA.
Many accounts, such as Google, Paypal, Facebook and Amazon, now offer the option of 2FA as part of their security settings. With 2FA, a security code is generated and sent to a second device via authentication app or text message for identification. Enter this code in your account to log in.
Attention: 2FA via text message can be hacked too. Therefore, we strongly recommend switching to a 2FA app as soon as possible. You can find out in a moment how this works in detail.
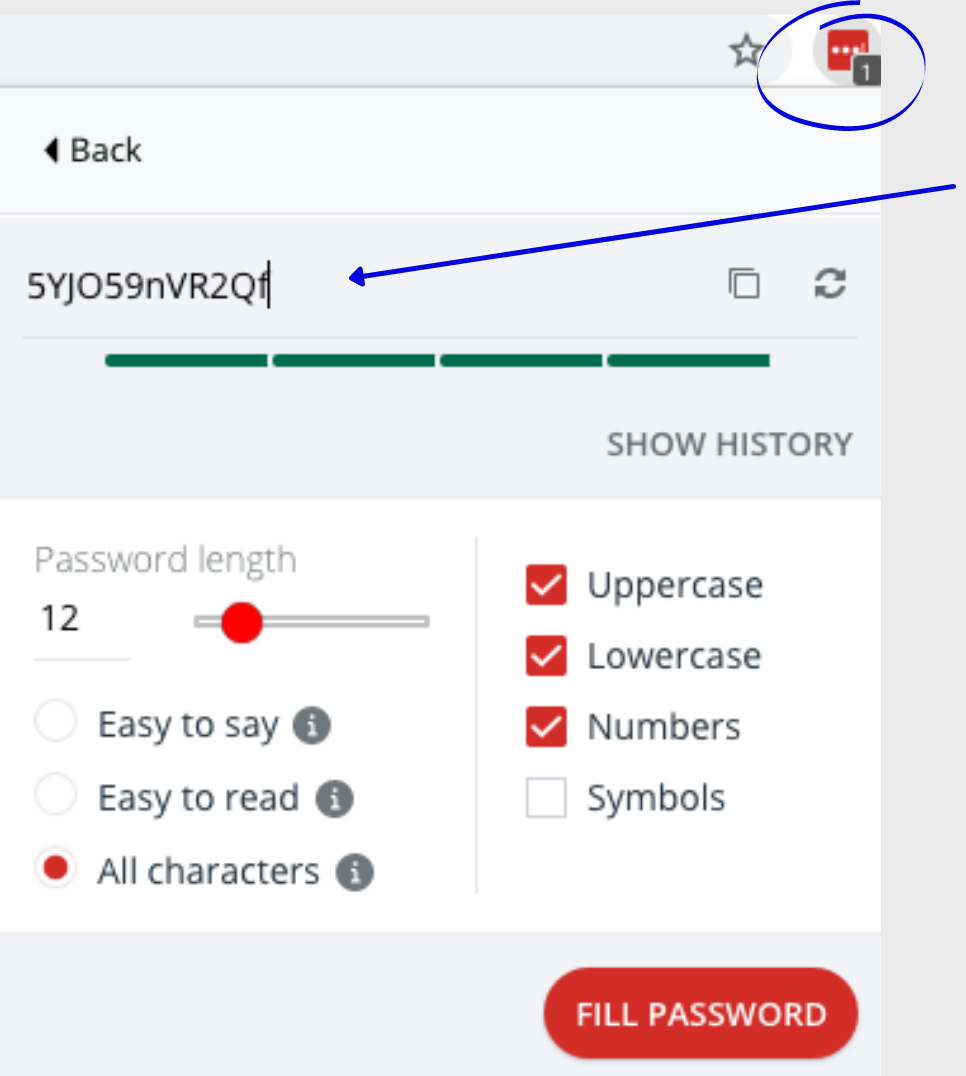
Note: What is a secure password?
A secure password may consist of a combination of upper case letters, lower case letters, characters and numbers. With a password manager, you can easily create passwords, save them and autofill via the browser extension or app. Forget the days of having to remember all your passwords yourself! Learn how to set up your password manager step-by-step below.
3. Use a Password Manager & Authenticator App
The highest level of security can be achieved by combining a password manager with an authenticator app. This way, you will have a secure password and a highly secure second layer of security.
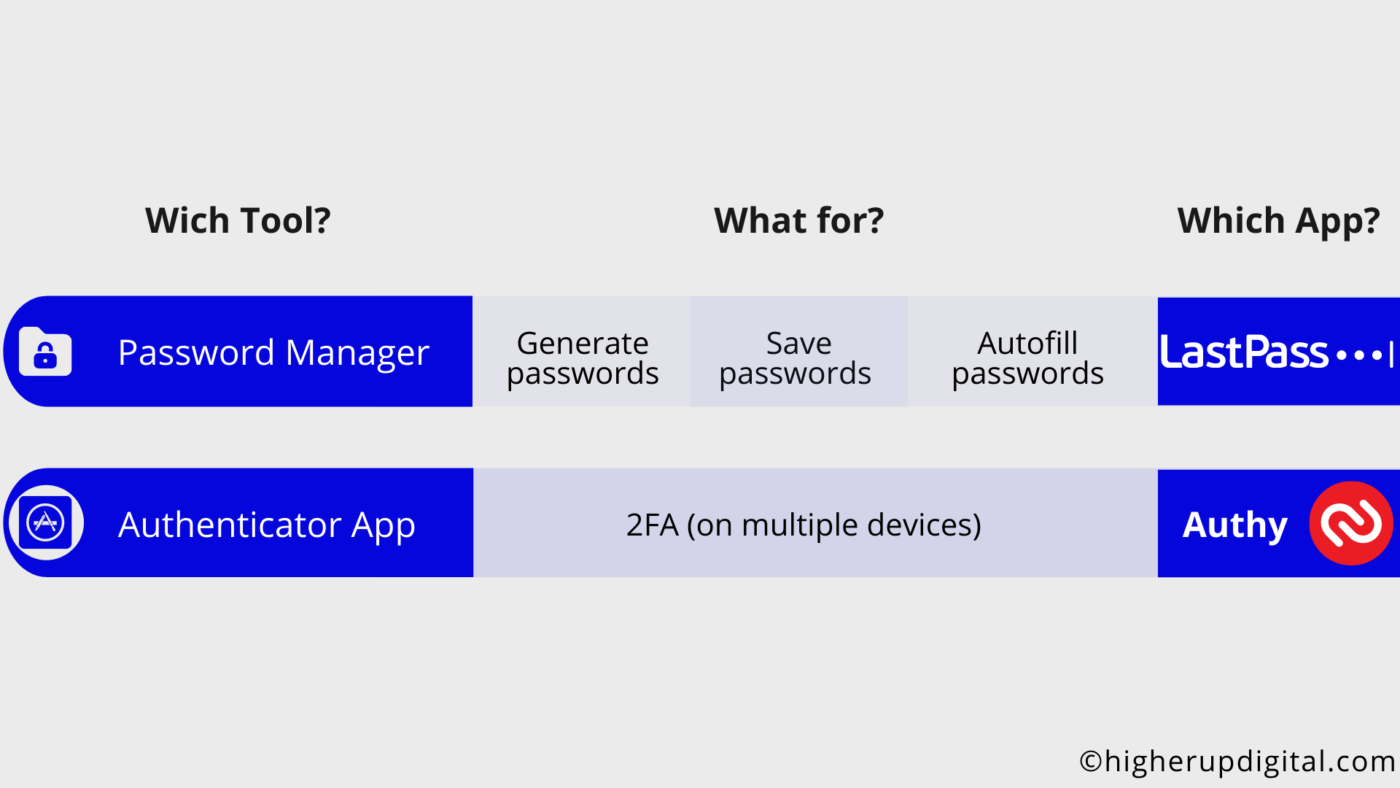
- Password Manager – A password manager is used to create secure passwords, storing them to have them available when you need them and autofill on your devices. We recommend a tool that is free in the basic version and has been tried and tested for many years, the LastPass password manager. It works as a browser extension or App for your smartphone – online and offline.
- Authenticator App – To use 2FA, you need an authentication app. As described before, a second device, such as a smartphone or tablet, will be used as a means of identification. We recommend Authy as a 2FA app. The major benefit here is that your account can be used on different devices. This allows you to operate multiple 2FA devices at the same time. The app works online & offline too!
4. Generating And Saving Strong Passwords With LastPass – How to Use It:
To set up LastPass, follow the steps below:
1. Get LastPass – Create an account with a secure password (so-called master password) and download the LastPass browser extension. Important: The master password will be often requested by LastPass. Therefore, be sure to write it down in a notebook or somewhere outside of your computer!
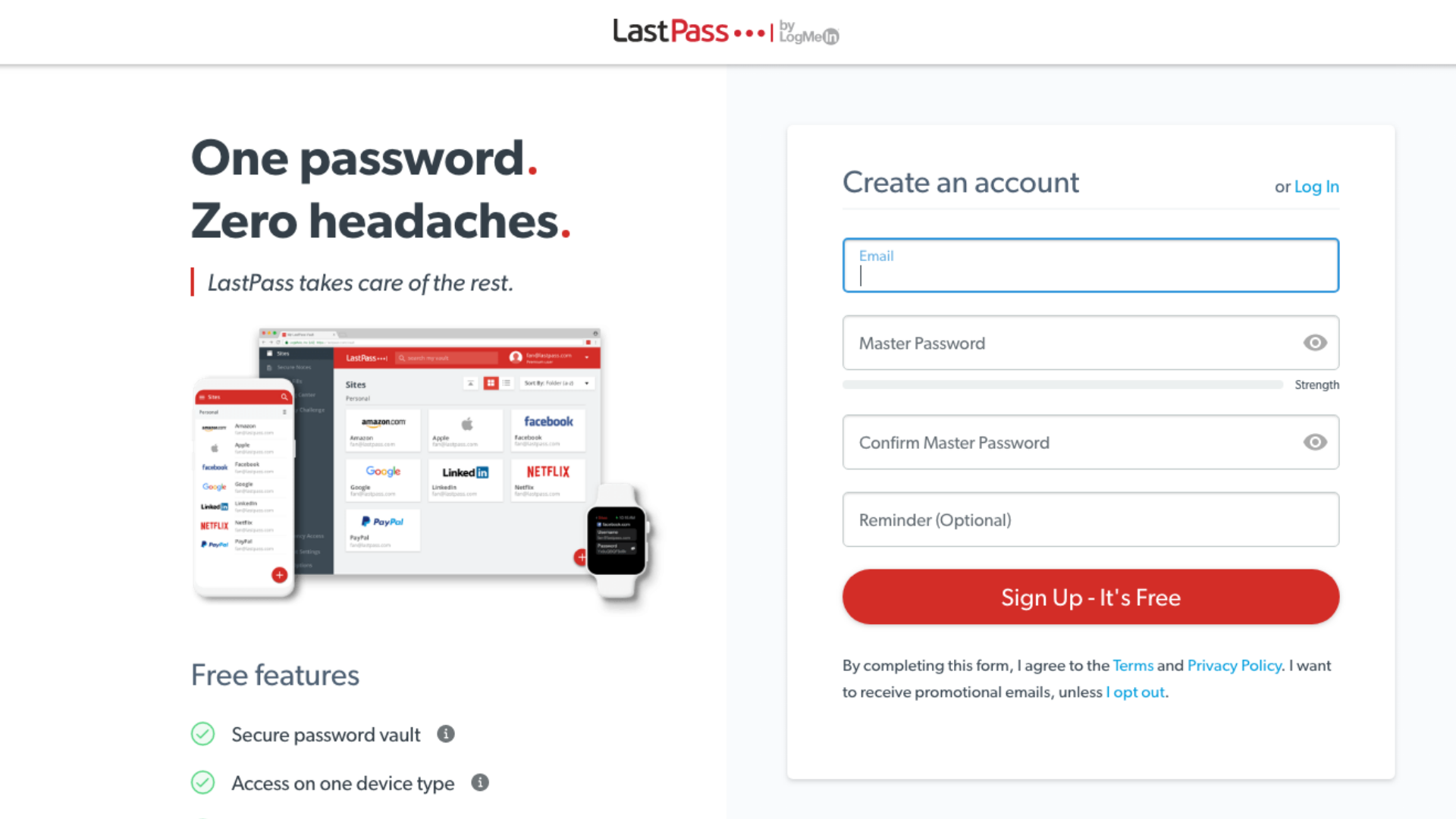
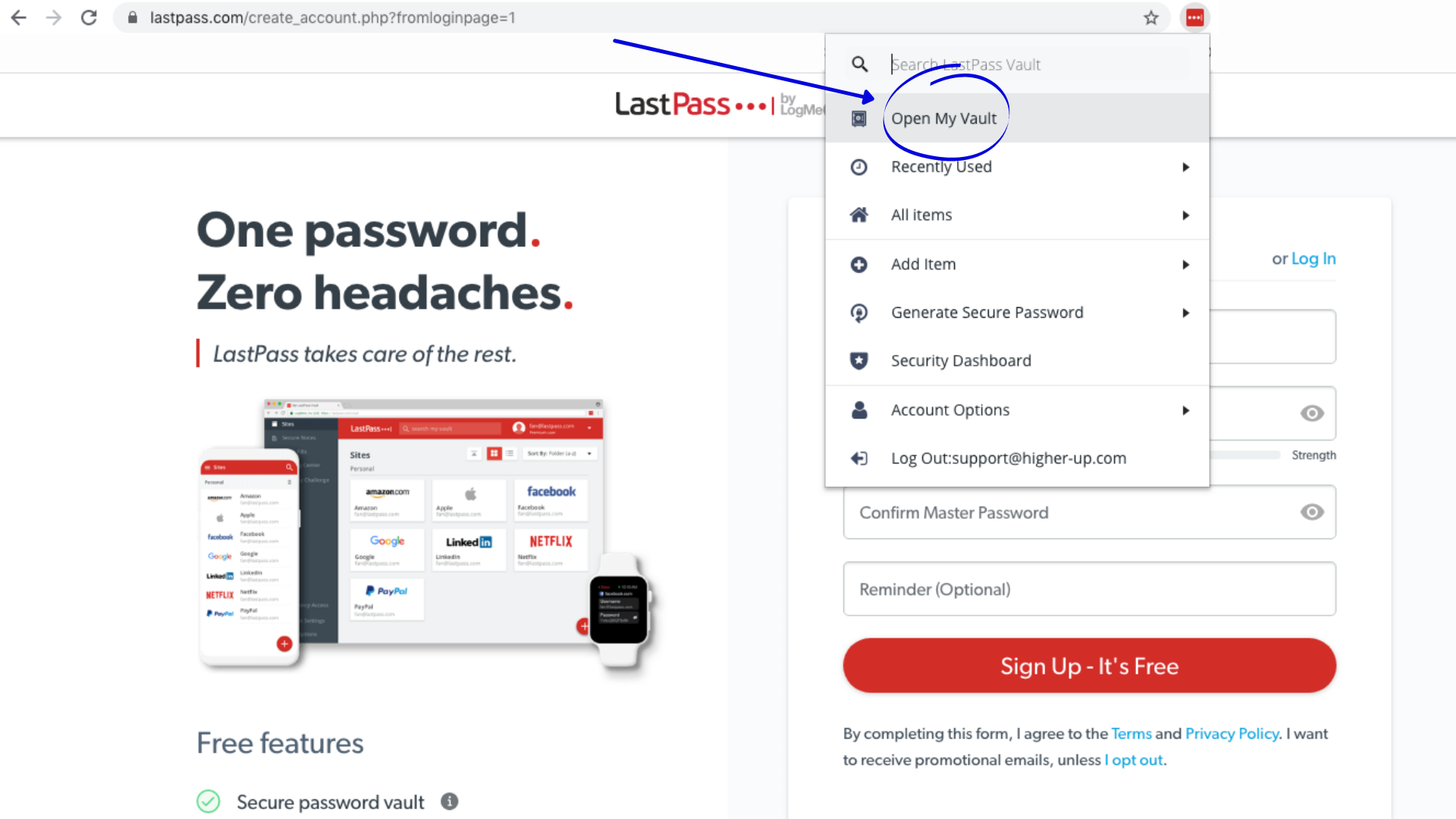
2. Your Vault to Save All Passwords – Then log in to your account via the browser extension and navigate to “Open My Vault”. From here, you can manage and organize all accesses.
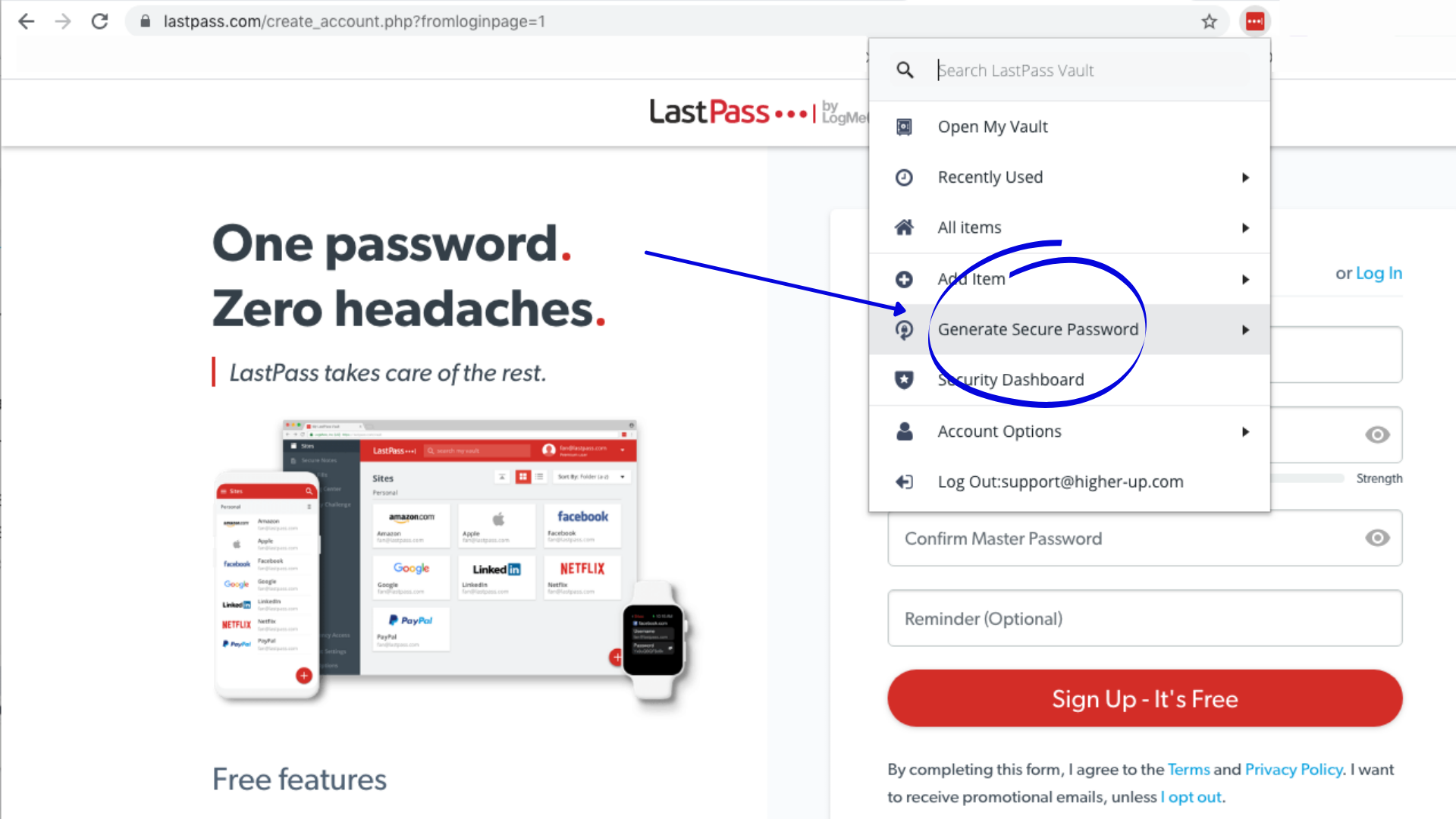
3. Generate Secure Passwords – By using the “Generate Secure Password” feature, you can create secure passwords, change them and then save them to your Vault.
When entering your log-in information on a website, LastPass will always ask if you want to save it to your Vault. This way, you have the option to update the saved passwords without actually having to open the LastPass Vault. This is super convenient, especially when logging in or creating new accounts.
Once you have created and set up secure passwords for all of your existing accounts, it’s time to double-secure the most important accounts using 2-factor authentication via an app.
At this point, you’ve finished an important step to keeping your accounts secure. Don’t forget… Insecure passwords are still the Nr.1 reason for account breaches!
5. Enable 2FA for Your Most Important Websites – How to Configure And Setup the Twilio Authy App
Authy ist an App by Twilio.com – one of the biggest and best-known companies for creating 2FA tokens. An Authenticator app generates a randomly generated 6-digit numeric code every 30 seconds which you will have to enter to log in to your accounts after being prompted for a password. The app works offline and only needs to be linked to your accounts once.
To use the Authy app for 2FA for your various accounts, proceed as follows:
- Download the app – Search in your App Store for the Authy App and install it on your smartphone and/or any other mobile device (e.g. iPad). Register with your email address to create an account.
- Enable 2FA for your accounts – Then set up 2FA for your accounts. We recommend to start with securing the accounts you previously evaluated as “most important”, such as email, Google, Facebook, PayPal, web hosting, etc.
You will first need the QR code of the accounts you want to add to Authy. The QR code is a barcode (square field with black characters and lines) that is scanned with the camera to pair the two devices. You will find the option to enable 2FA and the corresponding QR code in the security settings of most accounts.
Next, we will show you a few examples so you know what to look for:
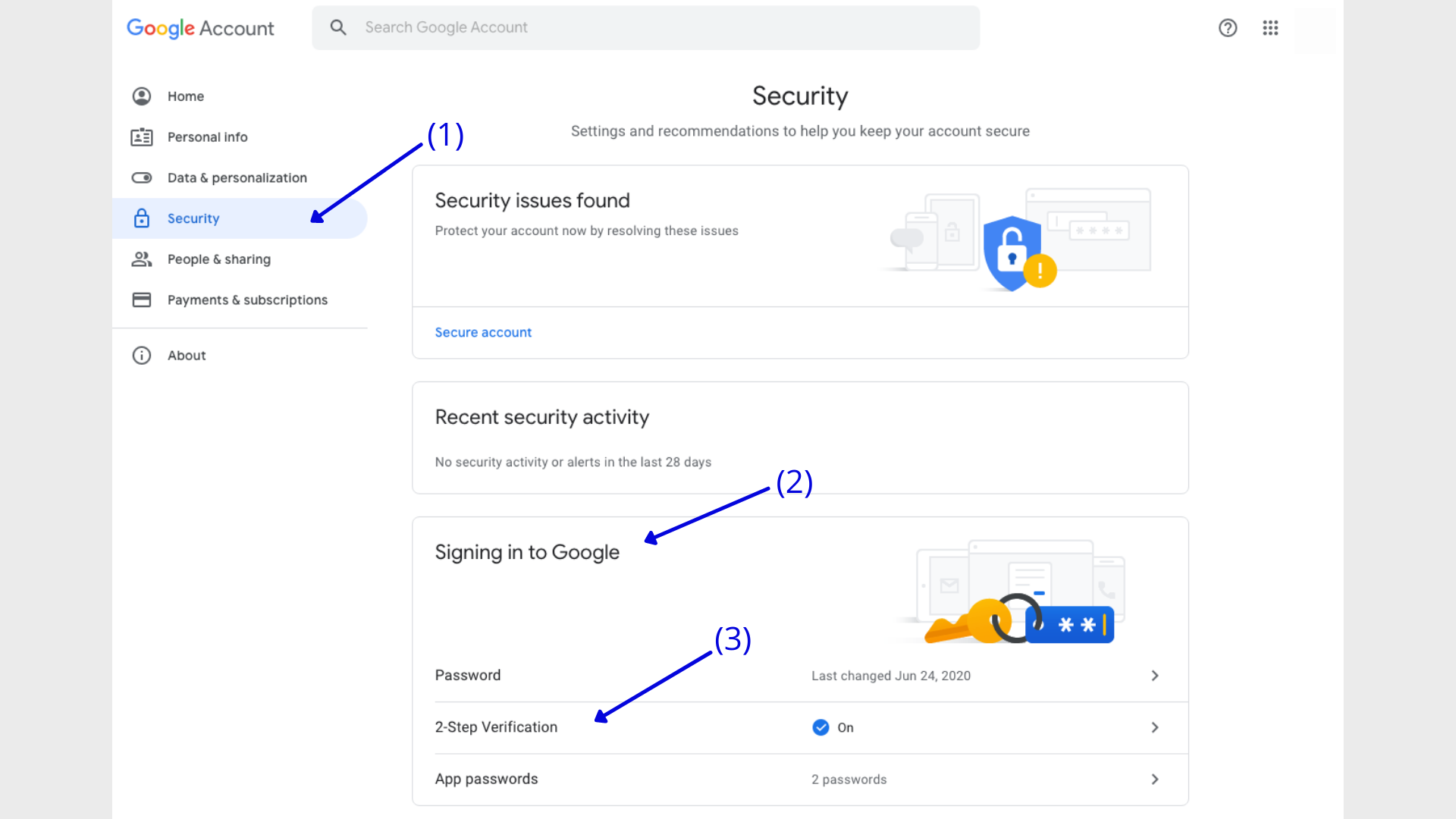
Enable 2FA For Your Google Account – To enable 2FA for your Google account, you need to sign in to your Google Account, go to “Security” (1), then “Signing in to Google” (2) and then click “2-Step Verification” (3). Choose “Authenticator App” here. You will then see the QR-Code.
To add a new account on Authy, click on “Add Account” in the main menu of the app on your smartphone or tablet.
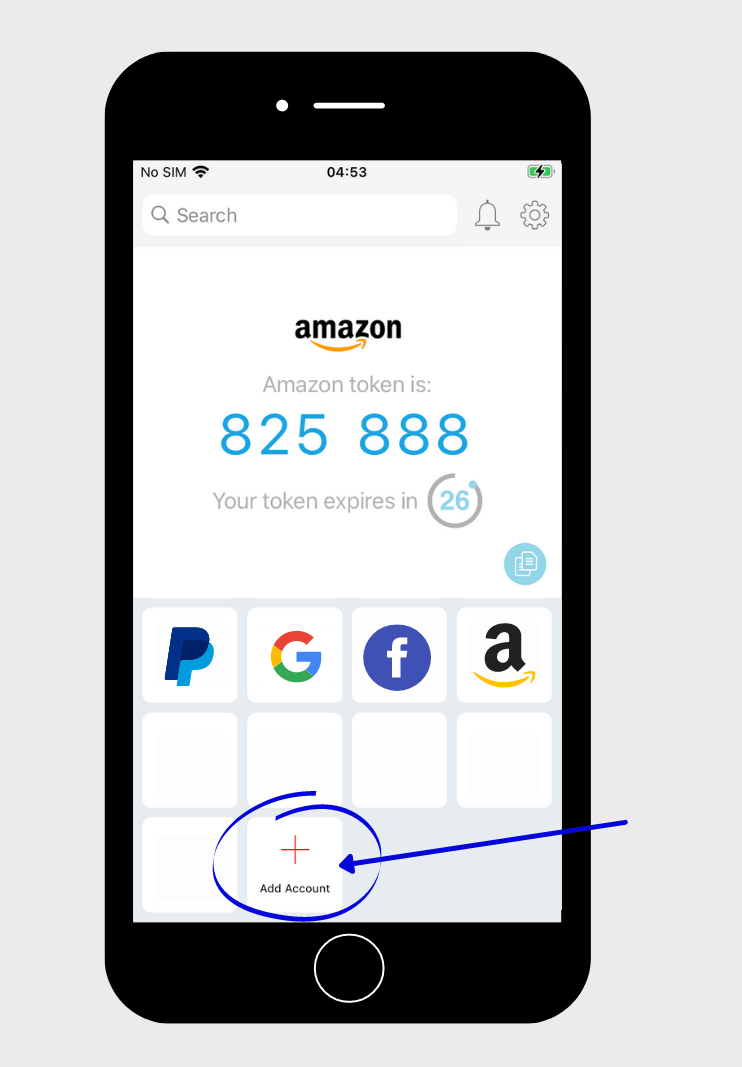
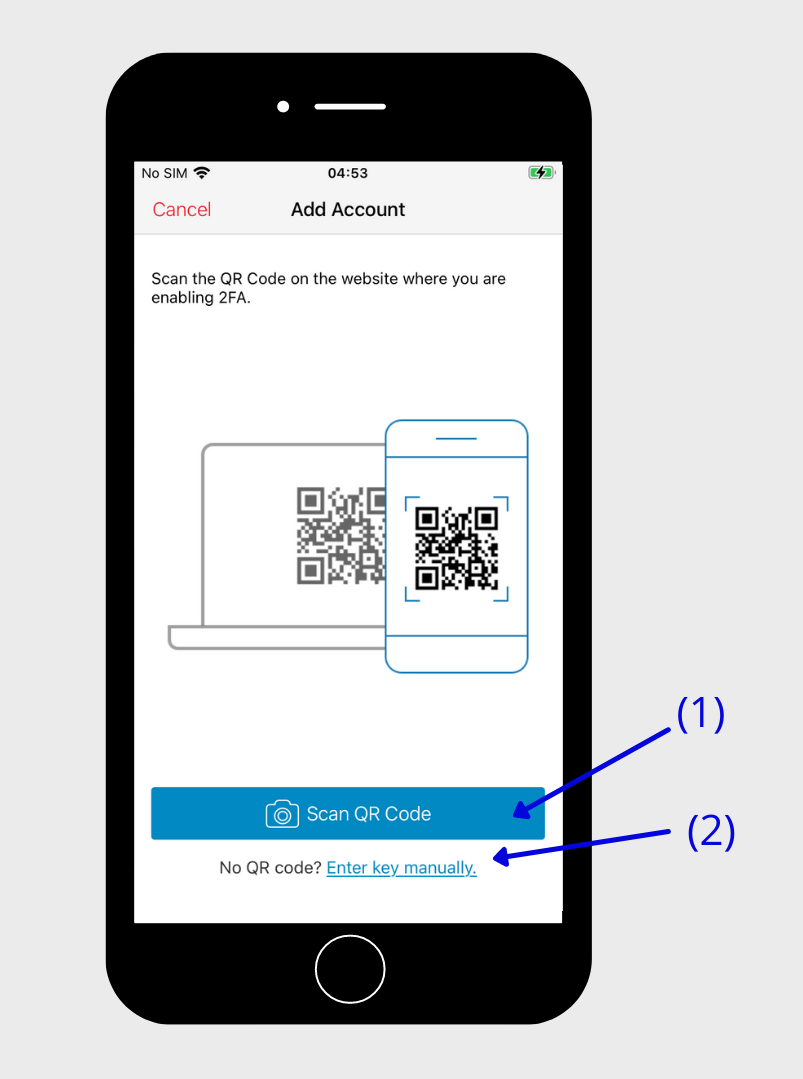
Then click on “Scan QR Code” (1) and scan the QR code that you got from the security settings of the account you want to add to the Authy app. You could also enter the “Private Key” by clicking on “Enter key manually” (2) if the service doesn’t provide you with a QR-code.
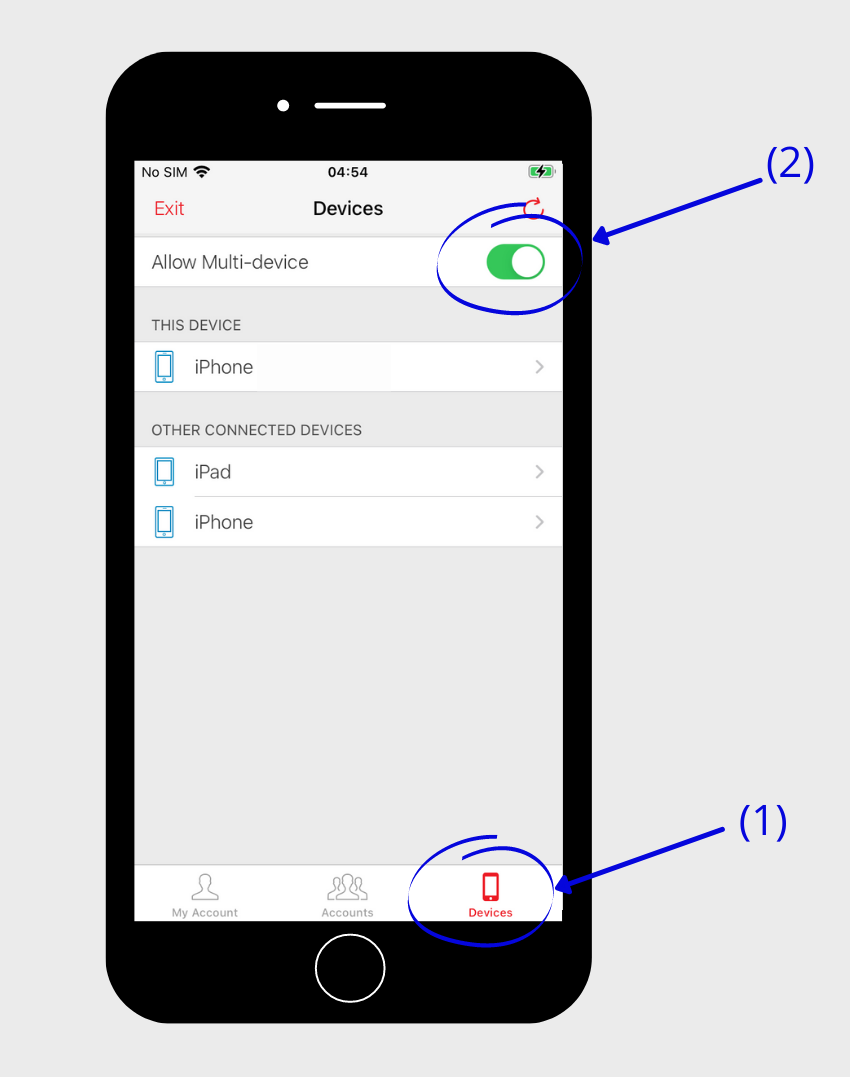
We recommend to synchronize the app to be able to use it on different devices at the same time, e.g. you on your smartphone while the accounting department uses another device.
Click on the settings symbol (gear icon in the upper right corner), then on “Devices” in the settings in the lower right corner (1) and enable “Allow Multi-device” (2).
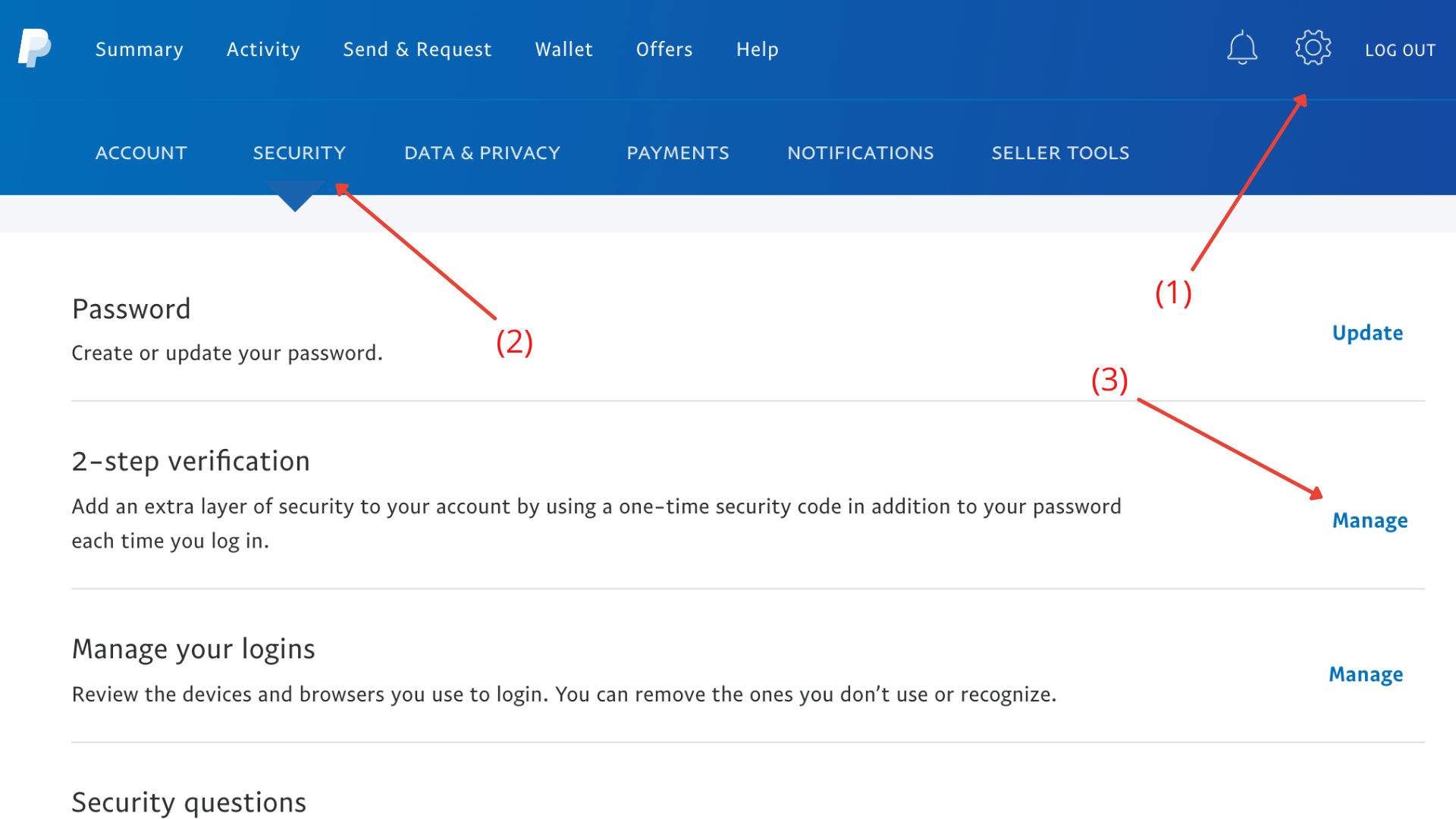
Enable 2FA for your PayPal account – With the same procedure you can also secure your PayPal account (or Stripe, Your Crypto Account or whatever accounts you are using).
First log in, click on the gear icon in the upper right corner (1), then click on “Security” (2) in the menu, then click on “Manage” (3) next to “2-step verification”.
Select “Authenticator app”.
Then follow the further instructions until you see the barcode on the screen.
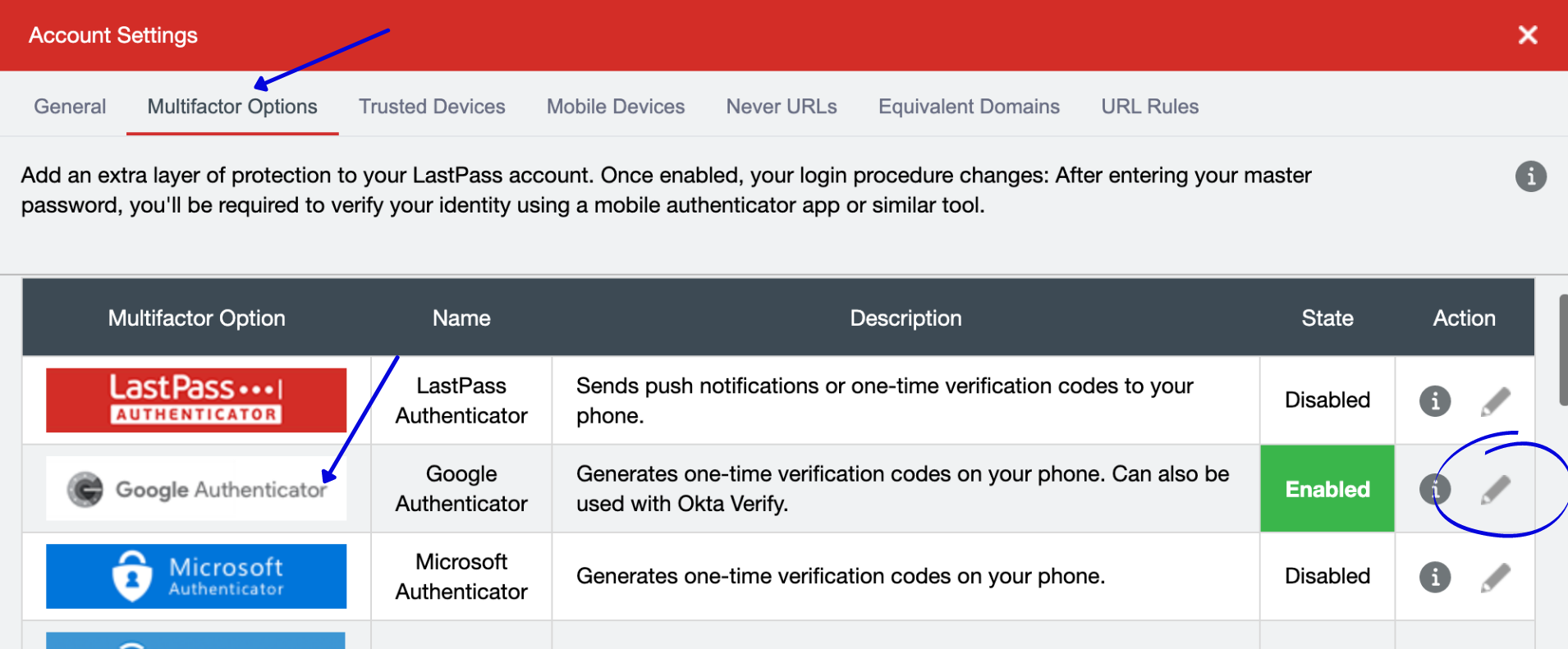
Setup and Configure 2FA for LastPass – We strongly recommend to also set up 2FA for your password manager login. To do this, go to “Account Settings” via your Vault.
Then click on the “Multifactor Options” tab. From there, click the edit icon next to Google Authenticator.
Note: Authenticator apps are compatible
In this post, we recommend the Authy app as it allows you to securely sync settings across multiple devices. The most popular alternative is Google Authenticator. The only disadvantage here is that the accounts are only linked to one local device and have to be set up again in case of loss of the device. Even if you can only choose the "Google Authenticator", Authy will also work!
Next to the “Enabled” option, select “Yes” from the drop-down menu (1).
Depending on whether you want or need to have offline access to your Vault, allow or deny offline access here.
We recommend to allow offline access as you might need to login to your Vault on your phone or browser without internet connection.
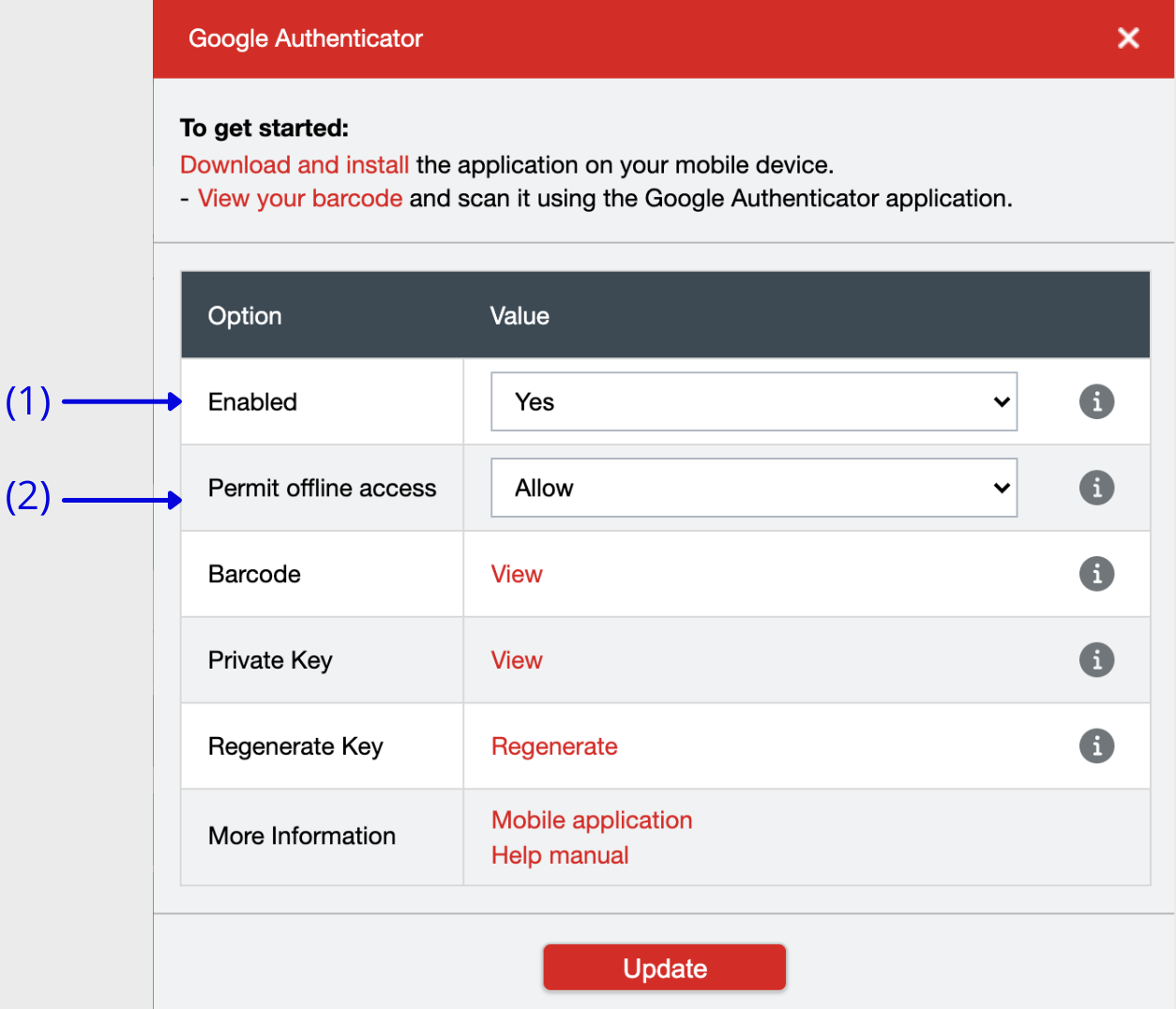
- Write down your private key – It appears when you click “View” next to “Private Key”. We recommend to write it down in a notebook outside the computer. This will serve as a backup in case you lose access to your Authy account.
- Display your QR code – Click “View” next to the “Barcode” option to have it displayed on your screen. Before that, however, you will be prompted to enter your password again.
- Scan the code with Authy – Open Authy and click “Add Account” at the bottom right. Scan the QR code. Lastpass will be added to your Authy account.
- Save all changes – After this, click “Save” in the Authy app. In LastPass, click “Update” to finish the process. Enter Lastpass password again if prompted.
This completes the setup of 2FA via Authy from LastPass. When logging in to LastPass in the future, you will need the Authy app for 2FA.
Congratulations! By using a password manager like LastPass in combination with Authy for two-factor authentication, your account will be protected against unauthorized external access. Your accounts are now well secured!
We provide Content Marketing & SEO Services for Your B2B Company
7 Extra Cyber Security Tips for More Safety
- Secure Wifi router access – The best password is useless if your Internet connection is insecure. Therefore, secure your router, both at work and at home. Make sure to use a secure WiFi password.
- Use guest access for IoT devices – Separate IoT devices from your office or home network (such as WiFi sockets or light bulbs). This can be done by using a separate router, or setting up guest-wifi access. This will ensure that third parties or hackers cannot tap data from your network.
- VPN for internet access in public places – When you are using the WiFi at a café or hotel when traveling, you should use a VPN app on your computer or smartphone. This way, your transmitted data is encrypted and cannot be viewed from the outside. We recommend NordVPN for this purpose. They provide an app for your smartphone as well as for your Mac or PC, through which you can easily turn on a secure internet connection that protects your connection.
- Secure handling of emails – Don’t click on links in email notifications, ever! Always log in to your accounts directly. This way you reduce the risk of falling for a phishing message. To make it easier to access your accounts, it’s a good idea to create bookmarks in your browser.
- Sending passwords securely – If you want to send a password to another person, then usually the first thing that comes to mind is sending it via text message. But this is not only insecure, you also have to give out your private cell phone number – which you might not always want to do. A better way to exchange passwords is using a secure self-destroying note which can be transmitted easily via a link. We recommend the free service from Safenote.co.
- Secure your website – We’ve seen it many times… Businesses put in endless hours of their time and invest tens or hundreds of thousands into their website and website content, but never bother to keep it secure! If you don’t properly take care of it, chances of your website getting hacked are quite high – especially when using popular CMS systems like WordPress.
- Backups are everything – Not only for your website, but also for your entire files and data, for example your files in your drive or other cloud service, a backup is a good idea. We recommend you always add a second layer of security and create backups with an external service. For Google Drive or Office 365 backups we recommend Afi.ai.
Increase Your Website Traffic Now
Conclusion - Don't Wait For Something Bad to Happen That Could've Been Prevented...
We recommend you carefully follow the steps of this guide to secure your online accounts and protect your data.
Getting hacked, losing access to your accounts, losing money or your identity and reputation is one of the worst things that could happen to you! Once it has happened, it can’t be reversed and you’ll regret not having taken action earlier. Unfortunately, many people highly underestimate the risk. We don’t – because we’ve seen it happen over and over again!
Cleaning up your accounts and your folders as well as setting up a password manager will also help you work much more efficiently!
If you’re finished optimizing your own setup, you should spread the word with your colleagues and your family!




